In order to strengthen the risk management of information security, the company has established information security unit to conduct risk management framework, formulated an information security policy, specific management plans, and invested resources in information security management. The details of police will be reviewed regularly.
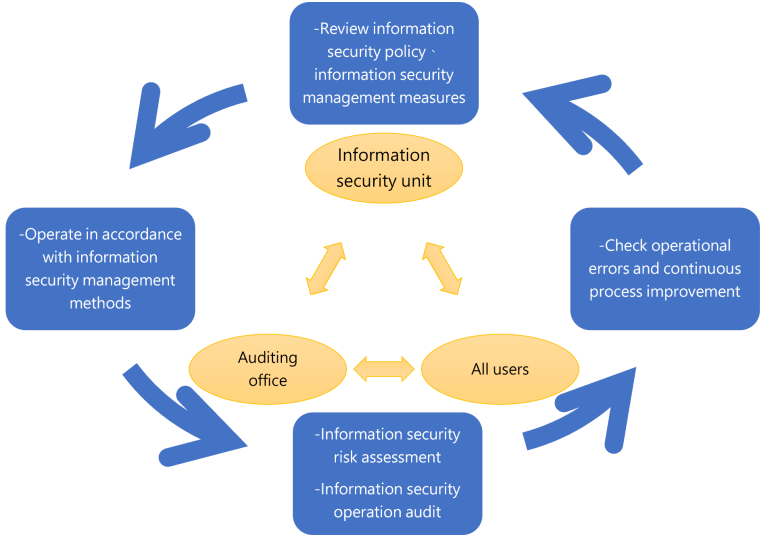
Information security Risk Management Framework
- The information security enforcement unit reviews information security management policies and related regulations regularly.
- All members of each unit are implemented in accordance with relevant regulations.
- Check servers and other equipment regularly during daily operations to discover problems immediately.
- Perform information security risk assessment and cooperate with the audit unit to ensure the integrity and effectiveness of the operation.
- In case of errors, loopholes and risks, immediate improvements are made to build a continuous improvement cycle for information security.
- The information security unit reports implement status to the CEO at least once a year.
Information Security Policy
1. The Purpose
This policy is specially formulated in order to strengthen the risk management of information security and ensure the security of data, systems, equipment and networks.
2. Information security goals
Ensure the correctness, availability, integrity and confidentiality of the company’s information security. Avoid the threat of internal and external information security incidents. In the event of an accident, it can also respond quickly and return to normal operation in the shortest time, reducing the damage caused by the accident.
3. Measurement of Information security
- Establish an information security unit to formulate information security policies and specific management plans.
- Personal information should be classified in accordance with the Personal Data Protection Law.
- Personal computers and servers need to set passwords, install anti-virus software, and update virus patterns irregularly.
- The relevant regulations on intellectual property rights should be observed, and private computer equipment should also be managed to ensure that all software installed is legally authorized.
- Important data should be backed up and the validity of the backup data should be confirmed regularly.
- Plan a Disaster Recovery Plan (DRP) to quickly restore system operation when an information security incident occurs.
- Perform information security advocacy irregularly to strengthen colleagues' awareness of information security and legal concepts.
4.Audit and revision
This policy is implemented after approval by the general manager of the group-company, and the same as revision.
Information security specific management plan
1.
2.
NDB group considers that information security insurance is still a new type of insurance. The company’s current information security risk management plan can effectively protect information security. Therefore, after evaluation by the information security unit, it is not necessary to purchase information security insurance at this moment.
NDB group’s specific information security management plan is distinguished by the time point of the information security incident, which can be divided into pre-prevention, daily operation maintenance, and trouble shooting. The specific management plan is as follows:
Category
Description
Content
Information Collection
Join TWCERT/CC
- Collect TWCERT information security intelligence.
- Vulnerabilities are patched.
- Participate in TWCERT courses to improve information security protection capabilities.
Prevent External Invasion
Install firewall and antivirus software
- Set up a network firewall.
- Install anti-virus software on the server and host computer.
- The virus code of antivirus software is automatically updated.
- Run anti-virus software scans every week.
Prevent data leakage
Account and authority management
- Personnel account review and management.
- Regularly audit the system authority settings.
Daily operation maintenance
Data backup and related inspection
- Base on the nature of data to run data backup, heterogeneous backup and remote backup.
- Perform data restoration tests regularly.
- Perform server host inspection and system testing daily.
- Regular computer inspections.
Information Security Incident Handling
Establish relevant operational procedures and recovery plans
- Establish cybersecurity incident response and reporting procedures.
- Formulate a disaster recovery plan.
- If there is no incident, the regular simulated training will be held.
- Improvement action and result will be conducted after DRP.
The company has invested resources in information security management since 2024
- Conducting an inventory and risk assessment of information and communication systems.
- The completion of Penetration Test.
- The completion of Social Engineering Drills.
- The completion of ERP System Authority Setting Auditing.
- The completion of Computer Inspection.
- The completion of Disaster Recovery Drills.
- External training hours for cybersecurity personnel: 53.7 hours.
- Conduct information security awareness and hold information security courses a total of 10 times.
Major information security incidents in 2024
There was no major information security incidents, such as violation of information security and leakage of customer information in 2024. There was also no case of legal action or any penalty associated with violation or loss of customer data.
Information security Risk Assessment
In accordance with Regulation of “Information Security Management” The company promotes various information security policies and implements various information security operations, supervises colleagues to follow information security standards, conducting information security risk assessment, inspecting operation deficiencies, and continuously process improvement to ensure that Information is fully secured. In addition, the internal control system of effectiveness assessment and information operation evaluation have carried out regularly every year to ensure its effectiveness. As a consequence, there is none of information security risk has found.
In order to strengthen the risk management of information security, the company has established information security to conduct risk management framework, formulated an information security policy, specific management plans, and invested resources in information security management. The details of police will be reviewed regularly.
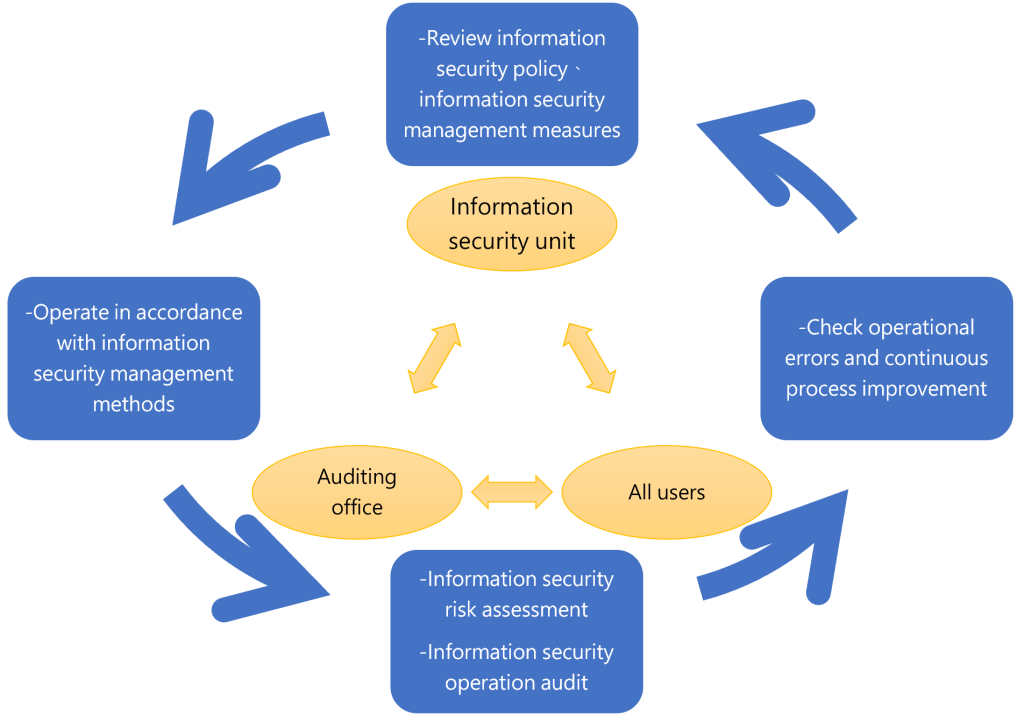
Information security Risk Management Framework
- The information security enforcement unit reviews information security management policies and related regulations regularly.
- All members of each unit are implemented in accordance with relevant regulations.
- Check servers and other equipment regularly during daily operations to discover problems immediately.
- Perform information security risk assessment and cooperate with the audit unit to ensure the integrity and effectiveness of the operation.
- In case of errors, loopholes and risks, immediate improvements are made to build a continuous improvement cycle for information security.
- The information security unit reports implement status to the CEO at least once a year.
Information Security Policy
1. The Purpose
This policy is specially formulated in order to strengthen the risk management of information security and ensure the security of data, systems, equipment and networks.
2. Information security goals
Ensure the correctness, availability, integrity and confidentiality of the company’s information security. Avoid the threat of internal and external information security incidents. In the event of an accident, it can also respond quickly and return to normal operation in the shortest time, reducing the damage caused by the accident.
3. Measurement of Information security
- Establish an information security unit to formulate information security policies and specific management plans.
- Personal information should be classified in accordance with the Personal Data Protection Law.
- Personal computers and servers need to set passwords, install anti-virus software, and update virus patterns irregularly.
- The relevant regulations on intellectual property rights should be observed, and private computer equipment should also be managed to ensure that all software installed is legally authorized.
- Important data should be backed up and the validity of the backup data should be confirmed regularly.
- Plan a Disaster Recovery Plan (DRP) to quickly restore system operation when an information security incident occurs.
- Perform information security advocacy irregularly to strengthen colleagues' awareness of information security and legal concepts.
4. Audit and revision
This policy is implemented after approval by the general manager of the group-company, and the same as revision.
Information security specific management plan
1.
2.
NDB group considers that information security insurance is still a new type of insurance. The company’s current information security risk management plan can effectively protect information security. Therefore, after evaluation by the information security unit, it is not necessary to purchase information security insurance at this moment.
NDB group’s specific information security management plan is distinguished by the time point of the information security incident, which can be divided into pre-prevention, daily operation maintenance, and trouble shooting. The specific management plan is as follows:
Category
Information Collection
Description
Join TWCERT/CC
Content
- Collect TWCERT information security intelligence.
- Vulnerabilities are patched.
- Participate in TWCERT courses to improve information security protection capabilities.
Category
Prevent External Invasion
Description
Install firewall and antivirus software
Content
- Set up a network firewall.
- Install anti-virus software on the server and host computer.
- The virus code of antivirus software is automatically updated.
- Run anti-virus software scans every week.
Category
Prevent data leakage
Description
Account and authority management
Content
- Personnel account review and management.
- Regularly audit the system authority settings.
Category
Daily operation maintenance
Description
Data backup and related inspection
Content
- Base on the nature of data to run data backup, heterogeneous backup and remote backup.
- Perform data restoration tests regularly.
- Perform server host inspection and system testing daily.
- Regular computer inspections.
Category
Information Security Incident Handling
Description
Establish relevant operational procedures and recovery plans
Content
- Establish cybersecurity incident response and reporting procedures.
- Formulate a disaster recovery plan.
- If there is no incident, the regular simulated training will be held.
- Improvement action and result will be conducted after DRP.
The company has invested resources in information security management since 2023
- Conducting an inventory and risk assessment of information and communication systems.
- The completion of Penetration Test.
- The completion of Social Engineering Drills.
- The completion of ERP System Authority Setting Auditing.
- The completion of Computer Inspection.
- The completion of Disaster Recovery Drills.
- External training hours for cybersecurity personnel: 53.7 hours.
- Conduct information security awareness and hold information security courses a total of 10 times.
Major information security incidents in 2024
There was no major information security incidents, such as violation of information security and leakage of customer information in 2024. There was also no case of legal action or any penalty associated with violation or loss of customer data.
Information security Risk Assessment
In accordance with Regulation of “Information Security Management” The company promotes various information security policies and implements various information security operations, supervises colleagues to follow information security standards, conducting information security risk assessment, inspecting operation deficiencies, and continuously process improvement to ensure that Information is fully secured. In addition, the internal control system of effectiveness assessment and information operation evaluation have carried out regularly every year to ensure its effectiveness. As a consequence, there is none of information security risk has found.